D2.3 – MVP Alpha (SHRUTHI)
tl;dr: 2021-12-09 – We are delighted to announce D2.3, the alpha release of Rhyzome, which marks the end of our third Milestone.
Introduction
Services hosting and system administration are integral elements in enabling community-run online group collaboration. The Self-Hosted, Robust Unikernel Testing & Hosting Infrastructure (SHRUTHI) effort encapsulates our exploration of this topic.
In D1.3 – SHRUTHI Service Prototype Release we were announcing
a practical and deterministic way for system administrators and collectives to self-host [DREAM] components.
Implementation
Based on our previous work, and incorporating subsequent refactoring to the Entanglement Garden self-hosting project, we have added private network provisioning for instances (VMs or Unikernels) with WireGuard endpoints for remote authentication and access.
This is implemented as the provisioning and resource management software Rhyzome.
Since D1.3, Rhyzome has been refactored into a modular system which consists of a core API that distributes jobs to purpose-specific components. We use the Rhyzome Libvirt component for provisioning instances (unikernels for VMs) paired with the Rhyzome Openwrt component to create and manage networks.
^ Basic diagram of SHRUTHI.
Instances (virtual machines or unikernels) may be clustered together into the same virtual network, allowing them to connect together directly in an isolated subnetwork.
Rhyzome API
This is the core of the system. It handles resource lifecycle management ans scheduling, and can be defined in two parts:
1. GRPC Server
All Rhyzome components connect to the core with gRPC, and use mutual TLS (mTLS) for authentication. Once components are connected, they wait for the server to send them jobs like creating new networks or VM instances.
2. HTTP API
This is how clients interact with Rhyzome. Allowing for a unified interface for CLI tools, web applications, or any other type of clients through a familiar REST API defined using OpenAPI specification.
Rhyzome Libvirt
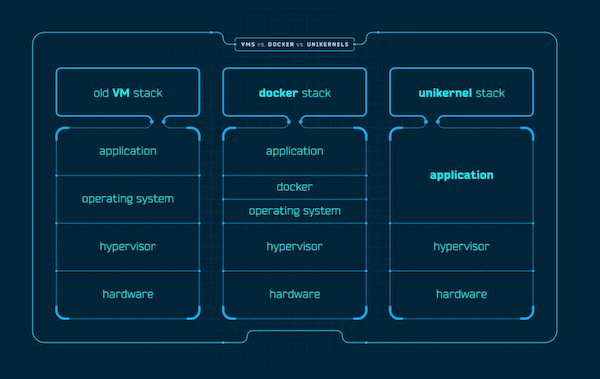
This component is for provisioning and maintaining computing instances using libvirt . Instances may either be general purpose VMs, or highly specialized Unikernels.
The component expected to be used on a Linux Hypervisor with KVM support, but may support other OSes in the future due to its relatively portable nature; Being written in Go, and based on Libvirt.
Rhyzome OpenWrt
A Rhyzome component which runs in an OpenWrt VM. It handles lifecycle management operations of networks and WireGuard servers.
Try it
You can try the implementation on any Linux system which can use KVM.
Please see the Getting Started guide for further details on installing and configuring Rhyzome.
Highlights
OpenWrt + WireGuard®
SHRUTHI uses OpenWrt Linux for its networking component. This provides a stable and well documented interface for managing subnets, firewalls, VPNs (WireGuard®), and VLANs due to OpenWrt’s UCI system.[1]
New networks have a WireGuard[2] interface created and bridged with them. WireGuard is a light-weight VPN implementation using modern cryptography. It was incorporated into the Linux 5.6 Kernel in 2020.
When you provision a network with Rhyzome, the OpenWrt bridge and WireGuard tunnel bundle enables system administrators to connect remotely from their office into the deployed VLANs like they would in their own datacenter. This allows for a proper separation in the case of professional hosting, where customers should only be allowed to see and connect to their own VLANs and VMs.
OpenAPI
Rhyzome’s API is defined using the OpenAPI specification. This allows for designing a maintainable API that can be easily consumed by tools and developers alike. You can find it in its own rhyzome-openapi repository.
Future
This alpha release of SHRUTHI is notable for the addition of several useful features, however there is still work to be done to make the provisioning software more generalized, and feature-complete. Work focused on UI & UX is needed to make the software more approachable and easier to integrate with 3rd party software.
Thank you!
We welcome feedback and criticism! Our forum is open for friendly cooperation among DREAM Catchers. Do not hesitate to contact us and contribute to the code: our research is made to improve the digital commons.
![]()
This is experimental software made within the DREAM project.
This project has received funding from the European Union’s Horizon 2020 research and innovation programme within the framework of the NGI-POINTER Project funded under grant agreement No 871528.
![]()